 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
TCP/IP Route Tracing Utility (traceroute/tracert/traceroute6)
(Page 2 of 4)
Operation of the traceroute Utility
Like the ping utility, traceroute is implemented using ICMP messages. However, unlike ping, traceroute was originally not designed to use a special ICMP message type intended exclusively for route tracing. Instead, it makes clever use of the IP and ICMP features that are designed to prevent routing problems.
Recall that the IP datagram format includes a Time To Live (TTL) field. This field is set to the maximum number of times that a datagram may be forwarded before it must be discarded; it exists to prevent datagrams from circling an internetwork endlessly. If a datagram must be discarded due to expiration of the TTL field, the device that discards it is supposed to send back to the device that send that datagram an ICMP Time Exceeded message. This is explained in much more detail in the topic that describes that message.
Under normal circumstances, this only occurs when there is a problem, such as a router loop or other misconfiguration issue. What traceroute does is to force each router in a route to report back to it by intentionally setting the TTL value in test datagrams to a value too low to allow them to reach their destination.
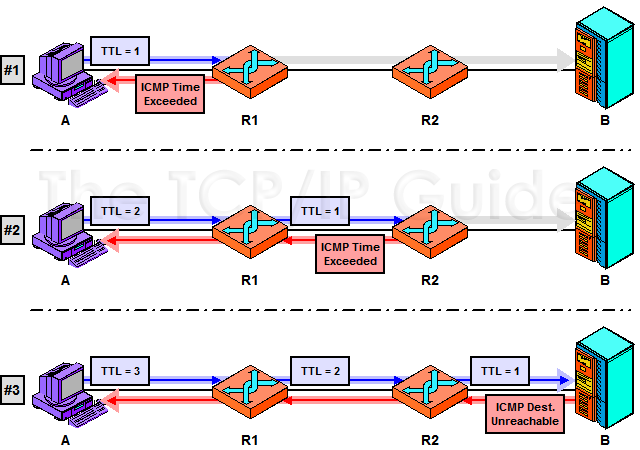
Suppose we have device A and device B, which are separated by routers R1 and R2—three hops total. If you do a traceroute from device A to device B, here’s what happens:
- The traceroute utility sends
a dummy UDP message (sometimes called a probe) to a port number
that is intentionally selected to be invalid. The TTL field of
the IP datagram is set to 1. When R1 receives the message, it
decrements the field, which will make its value 0. That router discards
the probe and sends an ICMP Time Exceeded message back to device
A.
- Device A then sends a second
UDP message with the TTL field set to 2. This time, R1
reduces the TTL value to 1 and sends it to R2, which reduces
the TTL field to 0 and sends a Time Exceeded message back
to A.
- Device A sends a third UDP message, with the TTL field set to 3. This time, the message will pass through both routers and be received by device B. However, since the port number was invalid, the message is rejected by device B, which sends back a Destination Unreachable message to device A.
This process is illustrated in Figure 321. Amusingly, we see that A sends out three messages to B, and gets back three error messages, and is happy about it! J The route to device B is thus indicated by the identities of the devices sending back the error messages, in sequence. By keeping track of the time between when it sent each UDP message and received back the corresponding error message, the traceroute utility can also display how long it took to communicate with each device. In practice, usually three dummy messages are sent with each TTL value, so their transit times can be averaged by the user if desired.
|
|
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.







 Key Concept: The traceroute utility takes the idea behind ping one step further, allowing not only communication between two devices to be checked, but also letting an administrator see a list of all the intermediate devices between the pair. It works by having the initiating host send a series of test datagrams with TTL values that cause each to expire sequentially at each device on the route. The traceroute program also shows how much time it takes to communicate with each device between the sending host and a destination device.
Key Concept: The traceroute utility takes the idea behind ping one step further, allowing not only communication between two devices to be checked, but also letting an administrator see a list of all the intermediate devices between the pair. It works by having the initiating host send a series of test datagrams with TTL values that cause each to expire sequentially at each device on the route. The traceroute program also shows how much time it takes to communicate with each device between the sending host and a destination device.