 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
PPP Network Control Protocols (IPCP, IPXCP, NBFCP and others)
(Page 2 of 3)
Operation of PPP Network Control Protocols
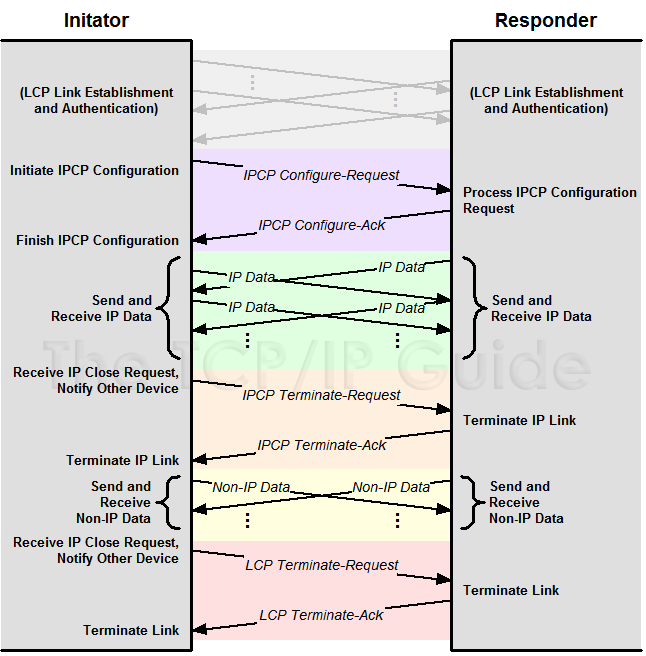
Each NCP operates very much like a “lite” version of LCP, as you can see by examining Figure 28 (and comparing it to Figure 26, which shows the messaging for LCP). Like LCP, each NCP performs functions for link setup, maintenance and termination—only it deals with its particular type of NCP link and not the “overall” LCP link. Each NCP uses a subset of seven of the message types defined in LCP, and uses them in very much the same way as the message type of the same name is used in LCP:
- Link Configuration: The process of setting
up and negotiating the parameters of the particular NCP link (once an
LCP link is established) is accomplished using Configure-Request,
Configure-Ack, Configure-Nak and Configure-Reject
messages just as described in the LCP topic, except these ones are particular
to the NCP. The configuration options are of course different; they
are the network layer protocol parameters being negotiated.
- Link Maintenance: Code-Reject messages
can be sent to indicate invalid code values (NCP frame types).
- Link Termination: An NCP link can be terminated
using Terminate-Request and Terminate-Ack. (Remember that
NCP links are set up within an LCP link; there can be more than one
NCP link open, and closing NCP links doesn't terminate the LCP link.
Also, NCP links do not need to be closed when an LCP link is terminated.)
Figure 28: PPP IP Control Protocol (IPCP) Message Exchanges
The overall operation of the NCPs, such as IPCP, is very similar to that of LCP. After LCP configuration (including authentication) is complete, IPCP Configure-Request and Configure-Ack messages are used to establish an IPCP link. IP Data can then be sent over the link. If the IPCP connection is no longer needed it may be terminated, after which the LCP link remains open for other types of data to be transmitted. It is not necessary, however, to explicitly terminate the IPCP link before terminating the LCP connection.
|
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.







 Key Concept: After the primary PPP link is established using LCP, each network layer protocol to be carried over the link requires the establishment of the appropriate NCP link. The most important of these is the PPP Internet Protocol Control Protocol (IPCP), which allows IP datagrams to be carried over PPP.
Key Concept: After the primary PPP link is established using LCP, each network layer protocol to be carried over the link requires the establishment of the appropriate NCP link. The most important of these is the PPP Internet Protocol Control Protocol (IPCP), which allows IP datagrams to be carried over PPP.